Microsoft, having given up on its own core browser technology, has released test versions of its Edge browser built instead on the same foundations as Google’s Chrome.
“In these first builds we are very much focused on the fundamentals and have not yet included a wide range of feature and language support that will come later,” said Joe Belfiore, Microsoft’s corporate vice president for Windows, in a blog post Monday. “You’ll start to see differences from the current Microsoft Edge including subtle design finishes, support for a broader selection of extensions and the ability to manage your sign-in profile.”
For years, Microsoft had tried to reclaim some of its browser power by stripping away the legacy technology that hobbled Internet Explorer and by releasing the modernized Edge instead. But it never caught on widely, and in December, Microsoft announced a plan to rebuild Edge on Chromium, the open-source underpinnings of Chrome that’s also used in several other browsers.
You can download the software for Windows 10 computers from Microsoft’s Edge Insider site. Different versions of Chromium-based Edge can be installed and run side by side.
The new version of Edge is based on Chromium, an open-source project run by Google. Other browsers that rely on Chromium include Brave, Vivaldi, Opera and Samsung Internet. Using Google’s software gives access to a mature and frequently updated software project while ensuring websites aren’t likely to suffer from incompatibility problems.
However, it also means Google’s already formidable power over the web — deciding in effect which technologies are supported and which aren’t — is that much stronger. Chrome dominates the browser market.
Apple’s Safari, a cousin to Chrome, and Mozilla’s Firefox remain independent.
Microsoft’s Internet Explorer dominated browsing for years, but Firefox dented that power 15 years ago and injected new life into the technology, even as Microsoft let it languish. Chrome arrived a decade ago, built on the same WebKit core as Safari. But Google parted ways, creating a fork of WebKit called Blink that’s the core part of Chromium.
By default, Chromium-based Edge sends search traffic to Microsoft’s Bing search engine, not to Google’s dominant search service. You can add other search engines if you want. Search traffic from browsers is an important financial consideration since they can lead to revenue from search ads.
Microsoft Edge improvements to Chromium
For now, the Chromium-based Edge is almost all Google’s code. But Microsoft plans to change that with contributions of its own, a potentially important shift in the dynamics of the Chromium community. So far, it’s contributed 275 changes to the Chromium project, Microsoft’s Edge team said in a separate blog post.
Some changes will be more obvious to users. Microsoft promised its Chromium-based Edge will get several features in coming weeks, including a dark mode, a reader mode for decluttered web pages, grammar and translation tools, and smoother scrolling.
Other changes are deeper under the hood. One big example is Microsoft’s work to build a version of Chromium-based Edge that runs on Windows laptops using 64-bit Arm processors, Belfiore said.
Most Windows laptops use Intel processors, but Arm chips — notably those built by Qualcomm — are part of a sustained push to design laptops with longer battery lives and built-in connectivity to 4G and later 5G mobile networks. To make that successful, Arm-based laptops need a full suite of software.
Microsoft also plans Chromium improvements in for touch-screen interfaces, video chat, graphics acceleration and accessibility — an important technology for people with vision or other disabilities.
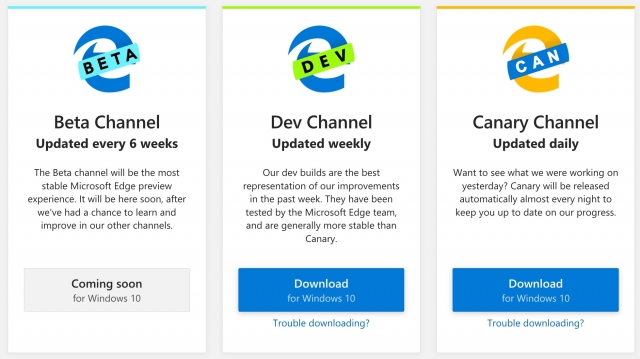
The Chromium-based Edge builds available now change rapidly — daily for the Canary version and weekly for the Developer version. Later will come Beta and Stable releases that should be more reliable. Those names follow Chrome’s labeling conventions. The Canary name refers to the canary-in-the-coal-mine idea for keeping a constant eye on whether something is going wrong.